一、Shiro整体概述
1.简介
Apache Shiro是Java的一个安全框架,功能强大,使用简单,Shiro为开发人员提供了一个直观而全面的认证(登录),授权(判断是否含有权限),加密(密码加密)及会话管理(Shiro内置Session)的解决方案.
2.Shiro组件
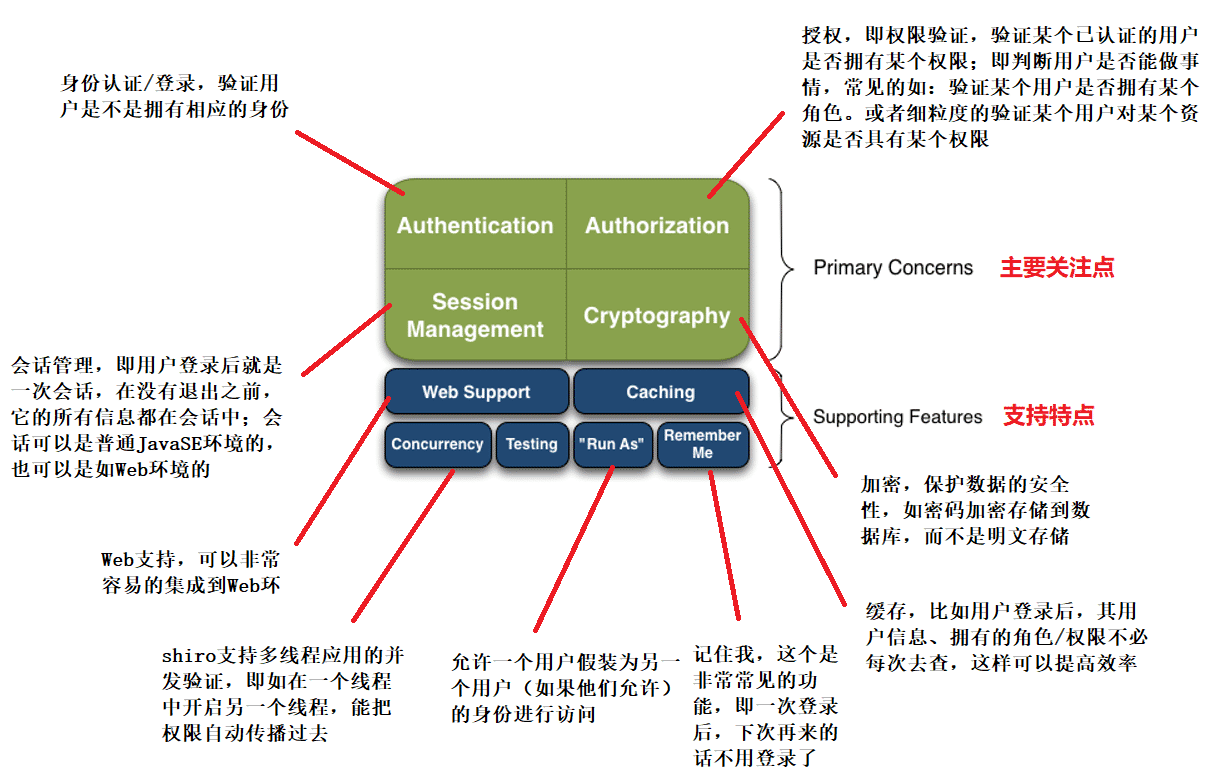
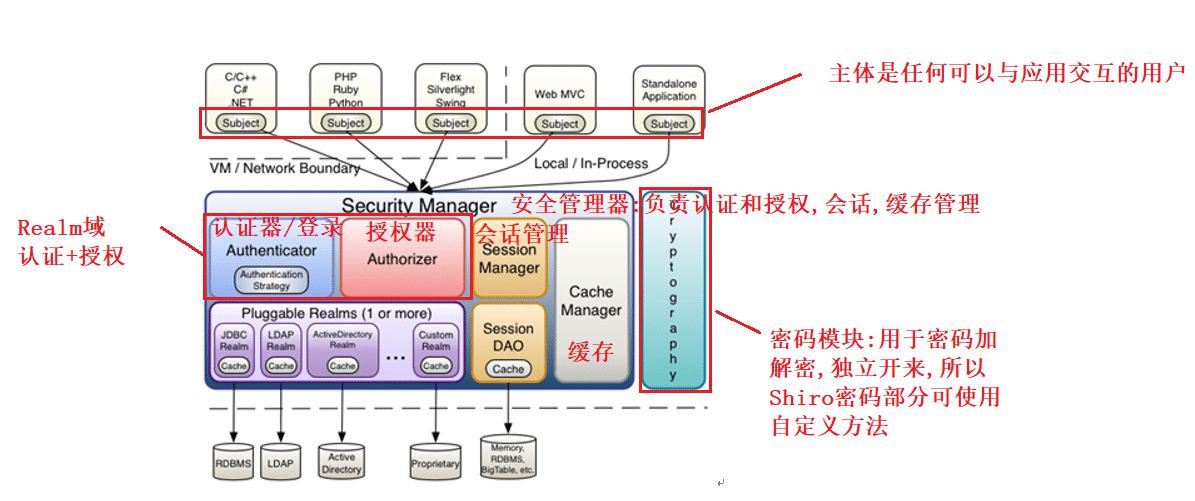
3.Shiro架构
3.1 外部架构(以应用程序角度)

3.2 内部架构
4. Shiro的过滤器
|
过滤器简称 |
对应的java类 |
|
anon |
org.apache.shiro.web.filter.authc.AnonymousFilter |
|
authc |
org.apache.shiro.web.filter.authc.FormAuthenticationFilter |
|
authcBasic |
org.apache.shiro.web.filter.authc.BasicHttpAuthenticationFilter |
|
perms |
org.apache.shiro.web.filter.authz.PermissionsAuthorizationFilter |
|
port |
org.apache.shiro.web.filter.authz.PortFilter |
|
rest |
org.apache.shiro.web.filter.authz.HttpMethodPermissionFilter |
|
roles |
org.apache.shiro.web.filter.authz.RolesAuthorizationFilter |
|
ssl |
org.apache.shiro.web.filter.authz.SslFilter |
|
user |
org.apache.shiro.web.filter.authc.UserFilter |
|
logout |
org.apache.shiro.web.filter.authc.LogoutFilter |
挑几个重要的说明一下:
anon:匿名过滤器,不登录也可以访问的资源使用,比如首页,一些静态资源等
authc:认证过滤器,登录成功后才能访问的资源使用
perms:授权过滤器,必须具备某种权限才能访问
roles:角色过滤器,必须具备某种角色才能访问
注意:这么多过滤器,使用起来肯定不方便,Shiro框架也考虑到了这一点,所以有一个过滤器,一个顶十个,即DelegatingFilterProxy.
5. Shiro与Spring整合
5.1 pom.xml
|
1
2
3
4
5
6
|
<!--shiro和spring整合--> <dependency> <groupId>org.apache.shiro</groupId> <artifactId>shiro-spring</artifactId> <version>1.3.2</version> </dependency> |
5.2 web.xml
|
1
2
3
4
5
6
7
8
9
10
11
12
|
<filter> <filter-name>shiroFilter</filter-name> <filter-class>org.springframework.web.filter.DelegatingFilterProxy</filter-class> <init-param> <param-name>targetFilterLifecycle</param-name> <param-value>true</param-value> </init-param> </filter> <filter-mapping> <filter-name>shiroFilter</filter-name> <url-pattern>/*</url-pattern> </filter-mapping> |
5.3applicationContext-shiro.xml
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
|
<?xml version="1.0" encoding="UTF-8"?><beans xmlns="http://www.springframework.org/schema/beans" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:aop="http://www.springframework.org/schema/aop" xmlns:context="http://www.springframework.org/schema/context" xmlns:jdbc="http://www.springframework.org/schema/jdbc" xmlns:tx="http://www.springframework.org/schema/tx" xmlns:task="http://www.springframework.org/schema/task" xsi:schemaLocation=" http://www.springframework.org/schema/beans http://www.springframework.org/schema/beans/spring-beans.xsd http://www.springframework.org/schema/aop http://www.springframework.org/schema/aop/spring-aop.xsd http://www.springframework.org/schema/context http://www.springframework.org/schema/context/spring-context.xsd http://www.springframework.org/schema/jdbc http://www.springframework.org/schema/jdbc/spring-jdbc.xsd http://www.springframework.org/schema/tx http://www.springframework.org/schema/tx/spring-tx.xsd"> <!--安全管理器,需要注入realm域,如果有缓存配置,还需要注入缓存管理器--> <bean id="securityManager" class="org.apache.shiro.web.mgt.DefaultWebSecurityManager"> <!--引用自定义的realm --> <property name="realm" ref="authRealm"/> <!--引入缓存管理器--> <property name="cacheManager" ref="cacheManager"/> </bean> <!-- 自定义Realm域的编写 --> <bean id="authRealm" class="com.itheima.web.shiro.AuthRealm"> <!-- 注入自定义的密码比较器 --> <property name="credentialsMatcher" ref="customerCredentialsMatcher"></property> </bean> <!-- 自定义的密码比较器 --> <bean id="customerCredentialsMatcher" class="com.itheima.web.shiro.CustomCredentialsMatcher"></bean> <!--缓存配置--> <!--内置(windows)缓存配置:MemoryConstrainedCacheManager--> <bean id="cacheManager" class="org.apache.shiro.cache.MemoryConstrainedCacheManager"></bean> <!-- filter-name这个名字的值来自于web.xml中filter的名字 --> <bean id="shiroFilter" class="org.apache.shiro.spring.web.ShiroFilterFactoryBean"> <property name="securityManager" ref="securityManager"/> <!--登录页面 --> <property name="loginUrl" value="/login.jsp"></property> <!-- 登录失败后 --> <property name="unauthorizedUrl" value="/unauthorized.jsp"></property> <property name="filterChainDefinitions"> <!-- /**代表下面的多级目录也过滤 --> <value> /system/module/list.do = perms["模块管理"]<!--路径和模块名称一定要和数据库表中存储的数据一致--> /index.jsp* = anon<!--anon 不登录也可以访问的资源--> /login.jsp* = anon /login* = anon /logout* = anon /css/** = anon /img/** = anon /plugins/** = anon /make/** = anon /** = authc </value> </property> </bean> <!-- 保证实现了Shiro内部lifecycle函数的bean执行 --> <bean id="lifecycleBeanPostProcessor" class="org.apache.shiro.spring.LifecycleBeanPostProcessor"/> <!-- 生成代理,通过代理进行控制 --> <bean class="org.springframework.aop.framework.autoproxy.DefaultAdvisorAutoProxyCreator" depends-on="lifecycleBeanPostProcessor"> <property name="proxyTargetClass" value="true"/> </bean> <!-- 安全管理器 --> <bean class="org.apache.shiro.spring.security.interceptor.AuthorizationAttributeSourceAdvisor"> <property name="securityManager" ref="securityManager"/> </bean> <!--支持Shiro注解配置--> <aop:aspectj-autoproxy proxy-target-class="true"/></beans> |
5.4 如果想看具体的实现代码(含sql脚本),可以点击页面右上角Fork me on github,到我的github仓库中拉取
仓库地址: https://github.com/AdilCao/Shiro.git
代码部分只需要关注三个类:
1.LoginController(登录,在这里获取Subject主体,调用subject.login()方法后直接调用认证方法)
2.AuthRealm(认证和授权在这个类中定义,认证成功后调用密码比较器进行比较;授权即查找登录用户所具有的权限模块集合)
3.CustomCredentialsMatcher(密码比较器,将浏览器输入明文密码加密后,与数据库中的安全密码进行比较)
注意:整个过程中如果登录不成功,就会抛出异常